Industrial control and automation systems need to maximize system throughput and quality of output, while at the same time managers are continually striving to lower operational costs. Engineers expect that the embedded software used in their industrial control and automation systems will run reliably with no downtime. This becomes a security and safety challenge as systems are becoming more data intensive and interconnect through Industrial IoT.
“We provide modern software solutions that allow you to meet these challenges with safety, security, and reliability being key.“
Accelerate development
Speed and accuracy without losing sight on reliability and security are key when designing the next generation of automation and control systems.
Increase Reliability
No downtime, no data corruption, no speed degradation when workloads increase, but yes to deterministic behavior and more flexibility without compromise.
Strengthen Security
Automation and Control Systems are part of the Industrial IoT. As such, they must be secure: from system firmware and boot process up to the application level.
Ensure Compliance
Functional safety of programmable electronic systems and machine control systems are inherent to their use. Development processes and coding therefore must be in accordance to industrial standards like IEC 61508 or ISO 13849.
Develop safer and more secure software systems
“What is the best way forward to implement functional safety and cybersecurity standards?”
Industrial & Energy and other sectors demand the use of functional and safety standards like IEC 61508, IEC 60730 or IOS 13849 and others. Complying with these standards using traditional manual methods can be time-consuming, costly and error-prone. As the size and complexity of software increase, the time it takes for manual methods to successfully complete the job, increases exponentially. The only way forward is to leverage certified software tools to help demonstrate compliance, and to add rigor and automation to your development process.
We help developers of security- and safety-critical industrial systems meet these software quality and test requirements with:
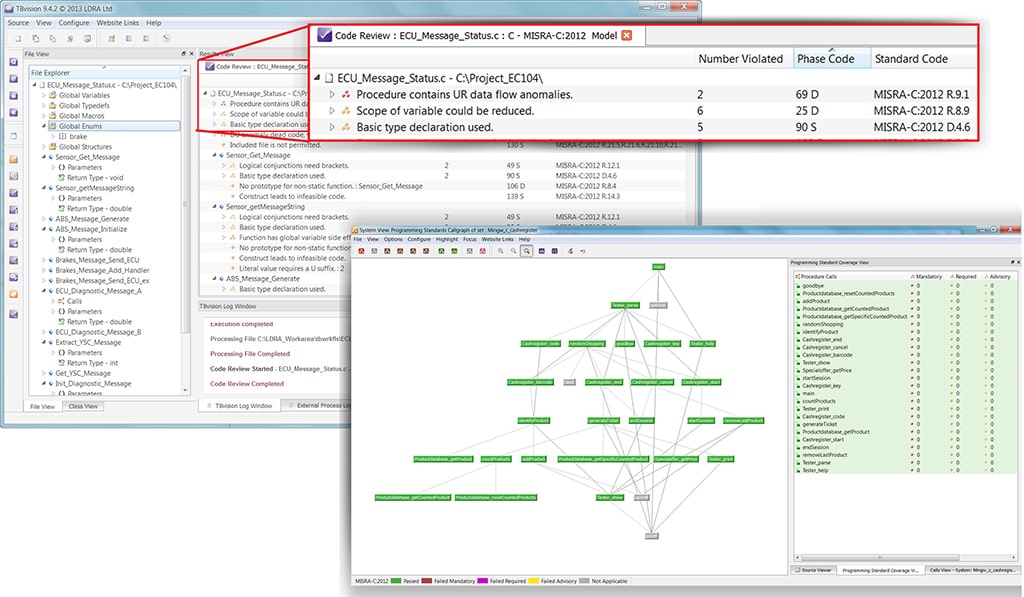
- Requirements traceability
- Coding standards compliance
- Structural coverage analysis
- Object code verification
- Unit, Integration & System testing
- Tool qualification
Coding Standards Solutions
Up to date device security
“How can I make sure that my software release doesn’t contain any security vulnerabilities?”
Remote monitoring of control and automation systems from beyond the corporate firewalls is becoming the de-facto standard. In many cases a (private) cloud environment is used as the link between system or plant owner and its home-bound employees, or the service department of the manufacturer of the system for maintenance and warranty purposes. It is not uncommon that many of the interconnected devices and systems contain open source up to some level.
How do you make sure that your systems are not vulnerable to hijacking or ransomware? Of course by making sure that they have the latest firmware. But how do you ensure that the latest release does not contain any (known) vulnerabilities?
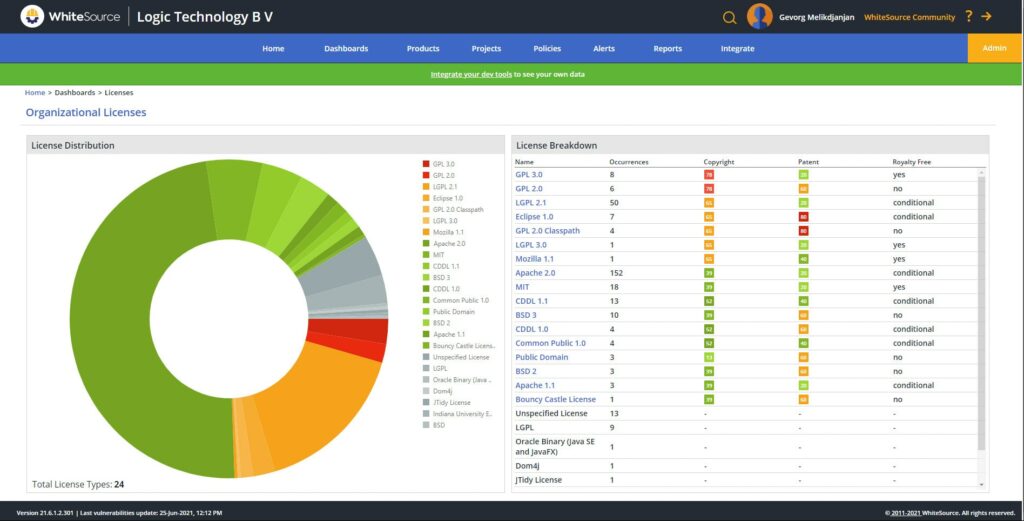
There is an intelligent solution for this problem identifying every open source component in your project:
- To ensure that you are not violating any license compliance
- To check if there is a validated newer release of the component
- To inform you of any known vulnerabilities in released component versions
- To help remediate the vulnerability or compliance breach
Software Architecture Analysis Tools
Flexibility with plug-in electronics
“What do professional coffee machines, Programmable Logic Controllers and building automation systems have in common?”
- These systems most often consist of a family or range of products with different connectivity options, HMI or user interfaces and displays, and they vary in performance. In many cases they use a common hardware platform, with firmware or applications originating from the same source tree.
- The product life cycle is long, and longtime availability of components must be guaranteed.
- They must be durable and operate in industrial environments.
Did you ever consider using industry grade plug-in Computer Modules? Ours check all the boxes:
- Our CoM’s are pin-compatible, making product variations in performance and memory capacity equal to a variation in platform pricing.
- They are based on successive generations of ARM processors , safeguarding product lifetime availability and feature extensions.
- They share the same Linux kernel build environments, making application porting easy.
Boards & Solutions for embedded development

Easy UI-design and product White Labeling
“how can we involve non-engineers in quickly adapting our UI design, for product variations and for ODM products?”
If your products range from low- to mid-end entry systems up to performant high-end systems, you may or may not want to use a common, recognizable front end User Interface. Or, if you are an ODM, you might sell the same electronics and system software in different boxes with different labels and a different User Interface. Perhaps your customer wants a (semi-) free hand in designing the UI for his device?
Did you ever consider creating a UI without the help of a software engineer? We have tools that make the life easier for everybody, by splitting the UI-design and underlying status and control functions and software:
- Product (marketing) managers can create a UI without software knowledge.
- Graphical Design engineers can use their favorite Photoshop application to create astonishing UI experiences.
- Software engineers can implement status and control functions independent from the graphical interface.
- Different UI’s can be seamlessly downloaded to the same system and application during runtime for run time and user experience testing.
- Change the look and feel of the UI without changing any code, makes branding and white labeling very easy.
Graphical UI Builder Solutions for Developers

Process data reliably at full speed
“Can we reliably distribute large amounts of different data types to our connected manufacturing devices?”
Today, data is essential at all levels in industrial automation and control systems and beyond. Whether it is recipe data that is pushed from an ERP system to individual controllers in a production or manufacturing line, or measurements from parameters in a production process, they share a common concern of corruption, loss or being accessed by unauthorized users.
In end-point systems, the reliability and validity of data starts at the hardware level; if the memory storage components fail or get corrupted, the device may fail or operate with scrambled settings. Most often flaky flash device drivers are the source of the problem. However, the right flash management driver will identify, correct or notify the application of possible issues.
We solve this eminent problem with industry grade flash memory management software:
Flash Device Manager for Embedded Systems
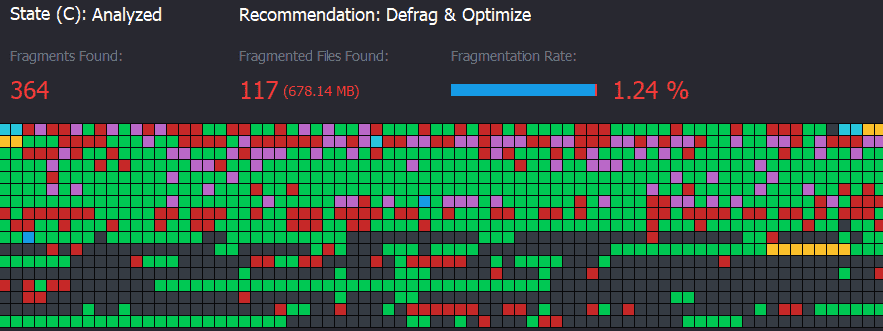
When storage media such as SSD or eMMC are used, the flash management part usually is not the concern, provided that they are of industrial grade quality, The concern there is the filesystem used to access the data on the media. Filesystems can get corrupted by power loss or failing memory. Especially in an industrial environment with sudden power shutdowns and surge spikes, this is a real concern for electronics engineers. Using a power safe, reliable filesystem is a must in these use cases.
An optimized transactional filesystem ensures that the data on the media is valid at all times, even when the power drops during a write action. With the right filesystem, you are guaranteed that the system reset or boot time takes exactly the same amount of time for a normal or sudden system restart:
File Systems for Embedded Devices
In Edge and enterprise systems, the volume of incoming and outgoing data as well as its transformations is increasing rapidly. Some of the data must be secured in a DBMS, other can be kept in volatile memory. Some data needs ultrafast transformation or calculations, and other data can be kept untouched in its original format on disk.
Ever considered the use of a hybrid DBMS? Its advantages are:
- Separate logging data from temporary data, causing less disk or flash memory transactions, thus increasing performance and prolonging media lifetime.
- Enabling ultrafast manipulation of data from volatile memory.
- Using SQL to manipulate the data in-memory or on-disc.
- Replicate transactional data to other devices in a failsafe environment
Databases for Embedded Devices


