Enterprise System and Internet of Things are the next advancements in technology that enable physical ‘things’ with embedded computing devices to participate in business processes for reducing manual work and increasing overall business efficiency. And it is all about data. Big Data processing and analysis, the insights derived from the IoT data sets, will become invaluable for the enterprise decision makers. Technologies such as real-time stream analysis and machine learning enable compelling scenarios including predictive maintenance and proactive monitoring of expensive industrial equipment. Besides the fact that this becomes a security and safety challenge, a flexible software architecture, the use of suited frameworks, and scalable DBMS systems are some of the cornerstones of a sustainable infrastructure.
“We bridge embedded and enterprise platform development with solutions that support both worlds”
Accelerate development
One ALM tool and no code barriers with one programming model for all architectures for fast and efficient heterogenous development
Increase Reliability
Start at the basis with rock solid testing and verification. Then Automate platform and data scalability and finish with Real time data replication to ensure availability.
Strengthen Security
The connection paths from sensor to gateway to cloud and enterprise applications can open many doors you better keep locked.
Ensure Compliance
IoT devices and Enterprise applications extensively make use of open source frameworks. Make sure that your applications don’t breach any license terms.
Increase HPC application development and performance
“how can we tune our HPC applications for maximum performance?”
When it comes to HPC, increasing the performance of applications helps increase the return on investment for HPC infrastructure. In many cases the software architecture, programming standard in combination with the compiler and libraries together determine the overall application performance. Finding the bottlenecks can be a tedious and costly process.
We can help your development team break through performance bottlenecks by making it easier to build high-performance parallel applications for HPC and AI. It empowers developers to apply the latest techniques in vectorization, multithreading, multimode parallelization, and memory optimization.
IDEs for Embedded Developers

Accelerate computing without the burdens of proprietary programming models
“We use heterogeneous platforms. Do we need a toolchain for each different core type?”
Today, a multicore system is the de facto standard. Whether there are more cores in a single die, commonly used in desktop and edge computing, or a series of CPU boards lined up in a clustered server system. In many cases they can be programmed with the same toolchain and perhaps an optimized cross compiler. But what when we throw a couple of GPU’s and some FPGA’s into the mix?
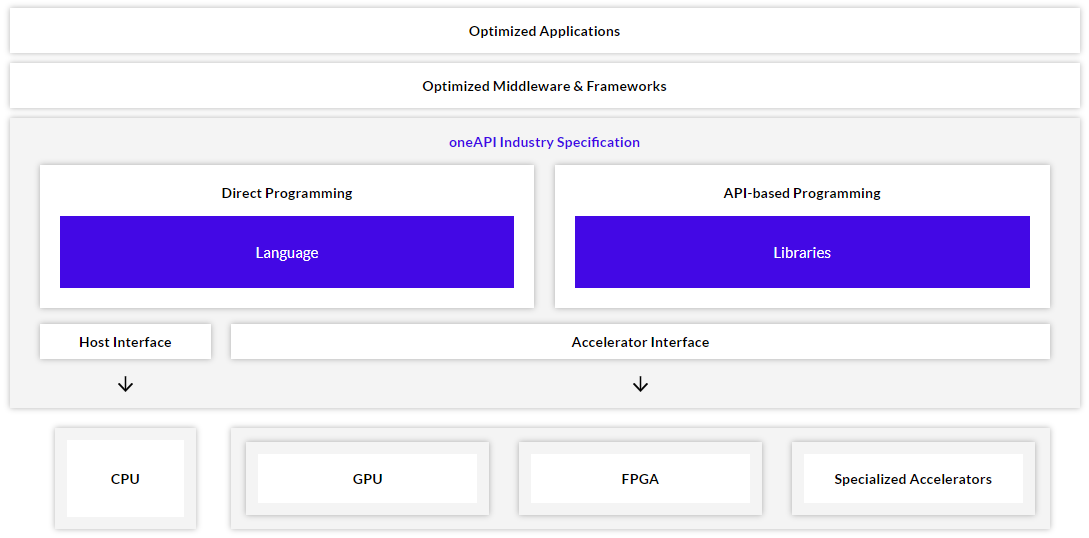
We support the cross-industry, open, standards-based unified programming model that delivers a common developer experience across accelerator architectures—for faster application performance, more productivity, and greater innovation. It extends existing developer programming models to enable a diverse set of hardware through language, a set of library APIs, and a low level hardware interface to support cross-architecture programming.
Intel® OneAPI Base Toolkit
The Importance of Open Source Security
“What are the main challenges in managing open source security & compliance on enterprise level?”
Whether it’s for large software platforms or interconnected embedded devices, open source components are the core building blocks of application software, providing developers with a wealth of off-the-shelf possibilities that they can use for developing their software faster and more efficiently.
Therefore, it’s imperative to use an advanced open source risk management platform throughout the entire software development life cycle. Thus providing developers and security professionals the tools they need to securely manage open source usage.
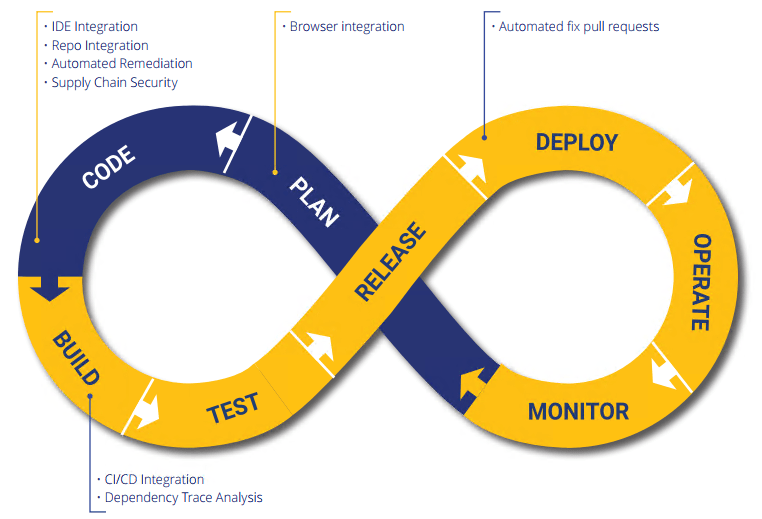
In order to achieve and maintain open source security from development to build to production and beyond, we have an advanced tool which contains the following functionalities:
• Enabling developers to code faster and more securely by focusing on automation, remediation, and prevention.
• Project teams need a powerful tool that integrates with top IDEs, repos, CI/CD tools, and bug trackers to help automate developer workflows,
leading with prevention and remediation to address security risks.
• Helping teams to shift security left by automatically preventing vulnerable components from entering organizations’ code base, with a browser integration tool that helps you choose secure versions.
• Continuously monitoring every open source component in production systems in your code base, including all direct and transitive dependencies, for newly discovered vulnerabilities, alerting users if a vulnerability is found in one of their components.
• Providing automated remediation advice so that open source components can be updated with confidence.
Open Source Software Composition Analysis
Significantly reduce build times
“Build times take up a substantial amount of our resources, how can we lower build times without investing in new hardware?”
For some developers, builds take up a lot of time and resources. This can become a problem, certainly when there are deadlines that need to be met, or when extensive testing is required to guarantee a certain degree of software quality. Our tools speed up compilation, testing and other computationally intensive tasks by distributing workload processes seamlessly and simultaneously to inactive CPUs in your local network or in the cloud. In essence, this build optimization tool seamlessly turns any host into a supercomputer with hundreds of cores and giga-bytes of storage.
No new computer capacities or additional VM / cloud services are necessary. Existing resources are used in an optimized manner and the same code, processes and tools are used to accelerate the process. Save enormous amounts of time by using embedded development solutions for enterprise by speeding up your compilation times.
Reduce build times and gain benefits during the entire Product Life Cycle:
- Avoid time pressure – shorten waiting times, accelerate compilations
- Switch off delays and sub-processes – optimize automatic builds
- Significantly reduce risks – process more cycles and increase quality
- Limit excessive investments – use existing resources
Build Time Acceleration solutions
Enterprise Grade SMB Implementation
“How to establish a high level of security in sharing files over a network to various devices at the same time?”
The SMB protocol is known for enabling applications or users to access files and other resources on a remote server. These resources can include file folders, printers, mailboxes, etc. It allows client applications to open, read, transfer, and update files on the remote server. It also allows communication between the client and any server program configured to SMB requests. However, some of the most destructive ransomware and Trojan attacks in history were based on SMB protocol vulnerabilities, which allowed them to spread in company networks and around the world. Therefore the evident question is how companies can enable an advanced and high-level approach to secured file sharing over a network? In order to help our customers achieve high security levels in their data transfers over the network, we have a software solution which is a high-performance, drop-in replacement for open source Samba and other SMB/CIFS servers.
With its modular design and the very first to deliver SMB compression to enterprise customers, the software boosts I/O throughput, reduces CPU usage, has a low memory footprint, and enables fast, easy handling of multiple simultaneous connections to shared resources. The “transparent” aspect of SMB compression is especially beneficial to end users, as no interaction is required on their part to compress or decompress files.
Above all, it provides capacity planning and management through quota support, as well as user audit and access log support and dynamic configuration of shares with no re-start required. It has no limits on volume size, file size, directories, or files except those imposed by the underlying file system. Based on the available system memory, the software can accommodate any number of clients.
Secure file sharing

Fast and scalable in-memory database system
“How can we maximize database speed, flexibility and reliability for our next project?”
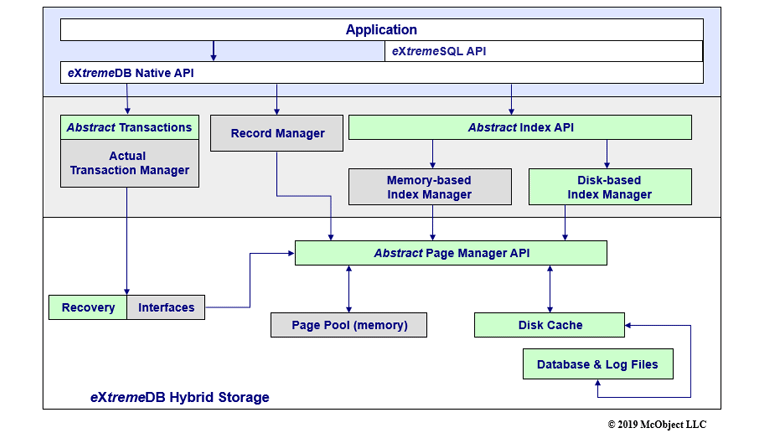
Are safety, security and scalability key aspects of your next embedded project? In that case you will often find that open-source database solutions like SQL might not be the best tools for the job. Logic Technology provides a tool that has proven to be the fastest hybrid persistent and in-memory database management system for edge and cloud. The software is highly suited for network infrastructure, embedded applications, IoT, big data & analytics and industrial automation. This database solution is blazingly fast, has a tiny footprint (under 150kb) and has a scalability to terabytes and supports the use of multiple CPU cores.
Below we have listed some core features of the software which are imperative for any project where fast data management is a priority.
- Database Architecture: In-memory database systems offer high performance and the possibility of very small RAM, CPU and storage demands.
- Multiple Database Index Types: . While the B-Tree is the best known index, many others can be more efficient in specific circumstances, such as geospatial/mapping and telecom/networking applications. Less well-known indexes include Hash table, R-Tree, Patricia Trie, Trigram and others.
- Cache Management: Our database system allows you to save the cache before shutting down a database, and to reload (or “pre-warm”) the cache on restart of the database.
- Pipelining: Without pipelining, interim results from each function’s transformation would be transferred back and forth between CPU cache and main memory, imposing significant latency.
- Data Compression: Database pages can be stored in a compressed format and decompressed when accessed by the application.
Database Management Solutions for Enterprise